Cyber security for machines
14 January 2019

Shutterstock image
The benefits of digitalisation are undoubtedly manifold. However, they also bring with them new problems and risks, the effects of which are best understood.
For example, hackers are increasingly targeting critical infrastructures and production sites. These attacks are made possible by the increasing digitalisation and networking of systems and machines. As a result, there are completely new "entry gates", which are actively used.
An example is the "Mirai" malware. This exploits the fact that more everyday objects such as routers, CCTV surveillance systems, digital video recorders, televisions, etc. are connected to the Internet (keyword "IoT" – Internet of Things). The malware constantly scans the Internet, looking for devices with security vulnerabilities; if vulnerability is found, malicious code is applied to these devices. The original "Mirai" botnet compromised around 500,000 IoT devices worldwide in 2016. Over three million devices are now trapped in the botnet! With the help of this malware, shortly before the US presidential election in 2016, an attempt was made to bring highly frequented web services such as Twitter, Spotify and Amazon to a standstill.
It is possible to paralyse the production of a factory on the one hand, and to use machines to attack other systems or to spread malware on the other.
The networking of machines continues to progress (keyword "Industry 4.0"). The network design seen in Figure 1 is still frequently used.
There are some shortcomings in this way of implementing networking.
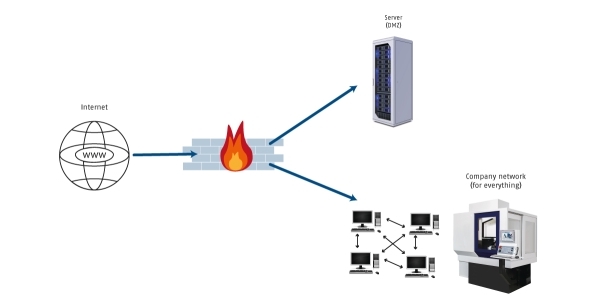
Figure 1
Many machine controllers use Windows or Linux operating systems. If real-time systems are also running on the same hardware, security updates are usually deliberately not carried out in order not to impair functionality. Also, such systems are not always equipped with anti-virus programs, as these can have a negative effect on functionality. For these and other reasons, a network with machines must be specially secured.
A possible solution is a network structure as shown in Figure 2. This network structure offers better protection of the industrial infrastructure with additional rules defined by the company's own IT group. These rules include:
• Subdivision of the production networks (factory floor) so that not everything is paralysed in the event of an attack.
• Any updates should be applied manually and in a targeted manner. Automatic updates could take place at the wrong time and lead to the failure of a machine during production.
• For industrial systems, the IT group should create special rules for updates and access to the Internet.
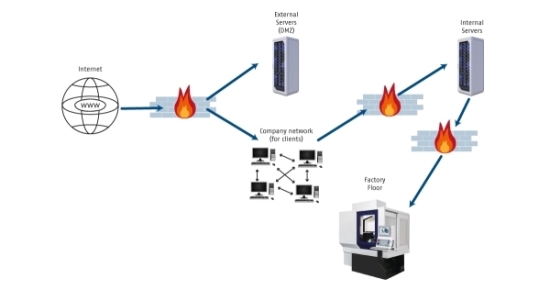
Figure 2
In the infrastructure shown, the firewall to the production network should also be set so that only "permitted" data packets are forwarded. Access of machines to the Internet is (mostly) not necessary, so this can be prevented.
Of course, the Internet is not the only concern when dealing with machine security. Attacks can also be made without using electronic networks. Malware can just as easily be introduced via memory sticks, flash cards, etc.
Today, a comprehensive analysis of a company's information security is the order of the day and the first step towards more protection against cyber-attacks. Various standards (e.g. ISO/IEC 27001) and process models (e.g. ISIS12) also exist on this topic.
Continuously retrofitting a machine control system with the latest operating systems is usually too expensive or technically not feasible without undue effort. It therefore makes sense to use such systems in an IT-protected area.
We are happy to support you in integrating NUM systems into your IT infrastructure and finding suitable networking solutions.
Contact Details and Archive...