2G switch-off and legacy device migration
Author : Tim Taberner, Technical Sales Director, Advantech IIOT
04 October 2023
As cellular technology advances towards mass 5G adoption, service providers are constantly looking for ways to optimise the use of the radio spectrum available to them. In recent years, it has become clear that one victim of this progression will be the provision of 2G and 3G services, which are now seen as out of date, of little commercial value, and which are therefore being withdrawn.
Some 2G networks have already been withdrawn, and in Europe a large proportion of the remainder are due to be switched off before the end of 2025. Indeed, in the case of 3G networks, this has already happened in many countries, even though, confusingly, the earlier generation 2G services will remain available for a short while longer.
The reason for this apparent contradiction is due to the operational characteristics of the two generations, from the perspective of data transmission. 3G systems marked the first generation where, from a user perspective, the interface was effectively the same as for any other IP-based network, albeit slower and somewhat unreliable.
Because of this, when 3G services have been withdrawn, all that has been necessary to migrate to LTE or 5G has been to replace the modems or routers with new-generation equivalents, with the change being transparent to any connected equipment, other than seeing an increase in performance and reliability.
2G migration complexities
This is not the case for 2G networks, where the way connections are established and data is transferred is different, and migration to later generations of cellular network is therefore more complex. Due to this incompatibility, 2G networks have been kept running beyond the end date of 3G systems, because the service providers are aware that, in the SCADA, automation and M2M workspace, many systems still rely on this technology, especially in the energy and utility industries.
Connected legacy devices are deployed which have many years of useful service life remaining, but which cannot directly access the IP-based communications mandated by more modern communication networks.
Time is of the essence
Time is however running out rapidly for these services. Some 2G networks have already been withdrawn, and in Europe a large proportion of the remainder are due to be switched off before the end of 2025, making this a very immediate and urgent issue for many users, given the time needed to roll out any new solutions. The question for owners of devices using these networks therefore is how to migrate to the newer LTE or 5G networks with minimum cost and disruption.
Of course, for some, this change will finally justify the replacement of the remote devices with more modern equivalents in order to take advantage of other new functionality available from them. For many, however, device replacement is seen as an expensive, high risk and disruptive operation, being forced upon them solely because of the need to migrate away from 2G cellular communications.
Thankfully for these system owners, there is an option available which can transparently migrate their existing 2G (and/or PSTN dial up) devices onto a modern ethernet, LTE or 5G network, allowing their legacy systems to continue to operate with minimal change or disruption.
Replacement system outline
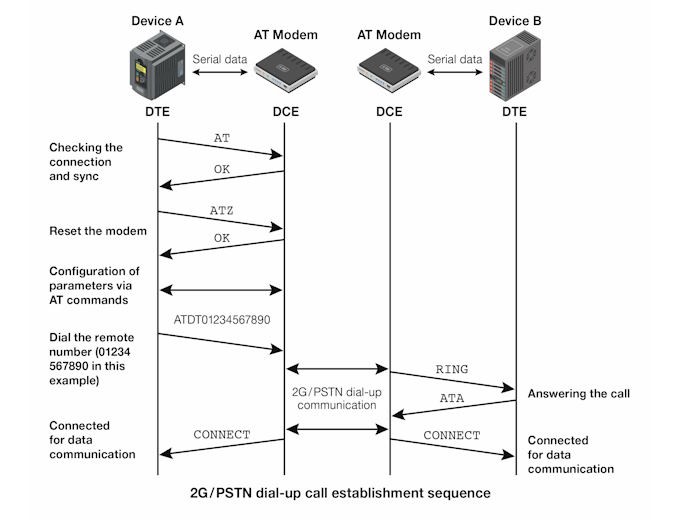
Figure 1: 2G/PSTN dial up call establishment sequence
In order to understand how this works, it is first necessary to understand the operation mode of most 2G-based M2M systems. This effectively mirrors the mechanisms used in landline-based dial-up PSTN networks, the connection sequence of which is summarised in Figure 1.
Each device is connected to a modem which uses a protocol known as the ‘Hayes’ or ‘AT’ command set. This defines a series of serial interface commands that can be used to obtain a connection to a remote device, transfer data across that connection, and subsequently disconnect the call.
In order to migrate these legacy devices onto an Ethernet, LTE or 5G network, what is needed is to effectively replace the AT modems with devices that support the AT command set via a serial interface, but which then can use an IP network to replicate the functionality of the dial-up system. This means that the connection / data transfer / disconnection command sequences need to be supported, but more importantly that a mechanism exists to create a virtual point-to-point serial connection through the IP network.
In reality, it is rare that only two devices are involved, and most of these systems have an architecture where a large number of remote devices will try to dial in to a single central server via one or more dial-up numbers. It is therefore also necessary to replicate concepts such as ‘number engaged’, in order to retain the same communications network characteristics at both the remote and server sites.
Advantech offers a solution to this dilemma using a combination of its edge routers loaded with an AT modem emulator application, and its WebAccess/VPN server. This solution allows for the seamless migration of equipment connected to legacy 2G (or dial up PSTN) systems onto current generation cellular networks.
The Advantech solution
WebAccess/VPN provides an authenticated and secure network upon which the system functionality is built (Figure 2). It allows creation and operation of a virtual private network (VPN) within the Ethernet or cellular communications system without requiring the user to have any detailed networking knowledge in order to configure and maintain it. Within the VPN, each router has a fixed and known IP address.
Importantly, any devices connected to the routers are also given visible, and optionally fixed, IP addresses, allowing interactions not only with the routers, but also between any devices connected to them. Primary access to the VPN can be via ethernet, Wi-Fi, fibre or cellular connection, with configurable options to automatically ‘failover’ between available connections, in the case of primary communications failure.
Each router is loaded with an AT modem emulator application. This configures a serial port that responds to the AT command set to create and destroy point-to-point tunnels between two routers within the network. These tunnels then transport any data appearing on a router serial port to the corresponding serial port on the remote router. This is analogous to a dial-up system, where a modem responds to the AT command set by creating and destroying point-to-point connections for serial data.
If the telephone numbers used within the third-party devices can be changed easily, then all a user needs to do is to change the phone numbers to the IP address of the desired destination router. If this is not easy to do, then scripting within each router can be used to convert the existing phone numbers provided by the third-party device to the corresponding IP address used within the network.
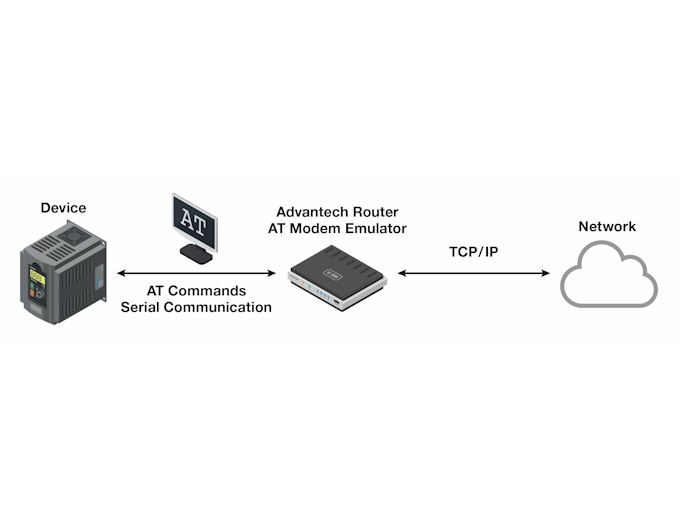
Figure 2: Device to cloud connection
The call connect/disconnect follows normal AT command principles, making the use of the IP network completely transparent to the third-party devices, which continue to operate as if they were still connected via a 2G or dial-up network. Importantly, the system is designed to be used in a point-to-multipoint configuration, typical of that found within SCADA networks (Figure 3).
The modem emulator has the following characteristics:
• Command ATD will create a tunnel to the corresponding remote router
• If the remote router already has a session in progress (with another router), then the call will not be answered (i.e. a router will only support one active ‘dial-up’ session at a time). This is the equivalent of the situation on a PSTN network, where a call cannot be completed to a number which is already in use (engaged)
• Once a call is established, whatever is received at the serial port on one router will be output from the serial port on the other router. The system is agnostic to the context of this data, so legacy protocol information between the SCADA endpoints is simply passed transparently
• If redundancy is required, then this works in the same way as for PSTN, i.e. there is a 1-to-1 correlation between an existing PSTN modem, and the router to replace it. In systems where the central system has a pool of available modems in order to reduce congestion, equivalence is achieved by simply replacing each host modem with a corresponding router.
Additional advantages of implementation
Once implemented, there are a number of additional capabilities which may be used to further leverage the system investment, albeit in some cases with some additional cost.
Remote router management
If WebAccess/DMP is included in the solution, then this will bring with it the benefits of zero-touch installation and remote management of the router estate. This will reduce the total cost of ownership of the solution, as well as provide future capabilities to deploy modifications or additional edge applications easily. In addition, WebAccess/DMP offers a full set of API calls, allowing its functionality to be accessed from any authorised and connected user application.
Remote third-party device management
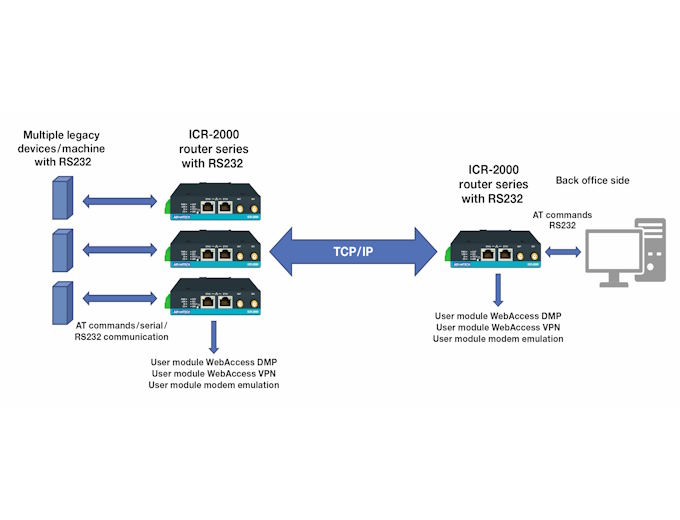
Figure 3: ICR200 schematic
If the third-party devices have a separate local configuration/diagnostics port, then this can be connected via the VPN to provide remote connectivity to the management system (for example from a standalone application running on a PC connected to the VPN).
If the configuration/diagnostics service is provided via Ethernet, then this can be directly visible through the router. If the configuration/diagnostic port is provided via a serial connection, then a second serial port on the router, or an external network attached serial interface can set up a terminal server connection via the VPN, allowing remote interaction.
Additional edge device connection
Whilst the described system aims at the migration of legacy 2G and dial-up data acquisition communications, once the routers and VPN are in place, they can be used to provide inter-site connectivity for other devices, using the always-on nature of the IP network, and the grouping/isolation features available from WebAccess/VPN.
These allow router and connected device visibilities to be restricted, based upon user profile, meaning, for example, that access to the router configuration can be restricted to the IT department whilst access to connected remote devices such as SCADA RTUs, PLCs, flow computers, etc. can be made available only to engineers in the operations department, with additional granularity possible to site, group or device level.
Note that this function is independent of the dial-up emulation. WebAccess/VPN working in combination with the routers provides not only fixed and visible IP addresses for each router but can be configured to provide visible (and optionally-fixed) IP addressing of any devices connected to the routers, allowing systems to interact directly with all IP-based devices on a remote site.
Use of router as edge device
The router has the capacity for additional applications to be installed. These may come from the existing range of user applications, can be developed as C code or Docker applications by the user, Advantech or third parties, or can use Python Scripting or NodeRED application framework downloads. Advantech and its partners offer a number of pre-existing edge applications, for example:
• to interface to legacy utility equipment using native protocols such as IEC 60870-5-101/103/104, DNP3.0 and Modbus
• to provide an IEC-61131 ‘soft’ PLC programming environment
• to interface to IT enterprise systems e.g. via MQTT for AI/ML inference
More information on Advantech here.
Contact Details and Archive...