How ready is your customer for Industrial IoT? Part 3: Industrial Security
29 June 2018
Shutterstock image
What do engineers need to know about the IIoT? This 3 part series by Cisco highlights priorities for planning your infrastructure readiness. Part 1 addressed how to bring automation, interoperability and intent to your network. Part 2 examined common misperceptions of industrial wireless. Here, Part 3 will address industrial security.
Securing your industrial network
Security – procedural, physical, electronic – remains the greatest barrier to (industrial) IoT adoption [see “Anatomy of an Industrial IoT Attack”]. However, IoT security isn’t just the Chief Information Security Officer’s (CISO) responsibility, it’s everyone’s.
How can you play your part, by designing secure industrial systems?
Firstly, plan a network with consistent policy and simplified segmentation across information technology (IT) and operational technology (OT). This approach will lead to faster detection and improved containments of threats, while managing the volume of IoT devices and their traffic requirements.
As the Anatomy of Attack video scenario demonstrates, the attack surface may just not be IT equipment (computers) but also sensors within an industrial network. An industrial demilitarised zone in combination with role-based, software-defined segmentation and enforcement will provide the level of security and assurance of intent-based networking required to manage bring-your-own-device (BYOD) configuration, and guest access.
For example, a plant-operations manager may have access to certain systems in an industrial environment via custom endpoints (a ruggedised tablet), but not to other industrial systems (based on business requirements and role function).
Secure remote analytics
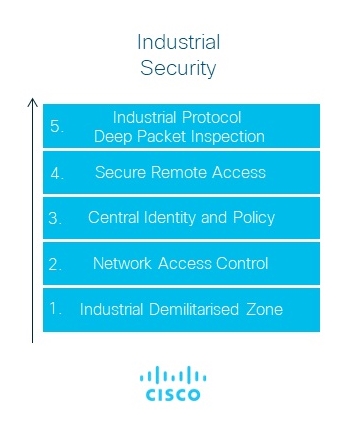
Industrial Security
Within the industrial-security stack, engineers must allow for a complete range of connectivity options, endpoints and platforms to meet customers’ remote access needs to allow highly secure, flexible secure mobility deployments for machine-to-machine (M2M) and worker devices through Virtual Private Networks (VPN).
Unlock network analytics to track IoT devices and leverage business rules to streamline workflows that notify personnel to take action in real time.
Encrypted traffic analysis now enables 99.95 percent of malware in encrypted traffic to be identified.
Anatomy of an Industrial IoT attack
“They didn’t scan the whole corporate network. The thermostat is connected to the entire corporate network...”
The Chief Information Security Officer scans biometric details, enters the research & development facility, connects the work laptop to the corporate network; the malware is then uploaded, enabling industrial espionage.
In this scenario, the hacker penetrates the enterprise since the factory thermostat was not protected by the industrial demilitarised zone. If this sounds like a plot from a film, it is! However, real-life intrusions have been attributed to similar IoT-based attacks.
There are broadly two approaches for identifying the security requirements of an IoT system. Consider the issue as a technical question, with the devices comprising a stack of layers, each of which has its own security needs which can be addressed by applying knowledge of how to secure similar computing systems. Or IoT devices can be considered as an opportunity and target for attackers. Knowledge of the likely tools and tactics of the attackers who will attempt to compromise the devices can be used to specify the defences.
Securing IoT systems against unauthorised connections by good network segregation and management either through keeping networks physically separate from other systems (industrial-demilitarised zone), software-defined networking or next-generation firewall protection, helps prevents criminal threat actors from accessing devices.
For more about how to plan a systematic approach to security, by taking the Open Systems Interconnection model as reference, see “IoT: what you need to know about how cyber criminals are exploiting this technology.”
So how ready are you?
1) Discover your industrial IoT readiness with a quick self-assessment
2) Take a customer checklist for industrial security [source: Cisco]
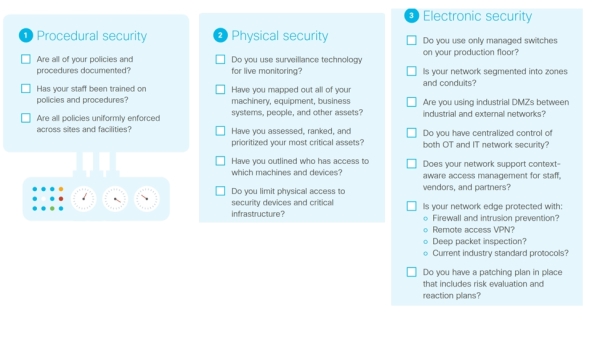
Cisco checklist
About Cisco and Routeco
Cisco provides the simple, intelligent, secure platform for industrial customers to improve business operations through Industry 4.0:
Routeco is an IoT Industry Expert Specialised Partner of Cisco. With experience of industries such as manufacturing, energy and utilities, travel and transport, connected safety and security, Routeco’s understanding of Cisco’s IoT platform provides industrial customers with the IoT solution they need.
About the authors:
Gordon Davies, Marketing Manager, Cisco with contributions from:
Cisco Industries Marketing
Cisco IoT Go-To-Market
Contact Details and Archive...